[EN] St. Pölten UAS | Multiple Vulnerabilities in Advantech EKI-15XX Series
Title: Multiple Vulnerabilities
Product: Advantech EKI-1524-CE series, EKI-1522 series, EKI-1521 series
Vulnerable version: <=1.21 (CVE-2023-4202), <=1.24 (CVE-2023-4203)
Fixed version: 1.26
CVE: CVE-2023-4202, CVE-2023-4203
Impact: Medium
Homepage: https://advantech.com
Found: 2023-05-04
By: R. Haas, A. Resanovic, T. Etzenberger, M. Bineder
Disclaimer: This vulnerability was discovery during research at St. Pölten UAS, supported and coordinated by CyberDanube.
Advantech EKI-1524/1522/1521 devices are prone to multiple Stored Cross-Site Scripting (XSS).
Vendor description
“Advantech’s corporate vision is to enable an intelligent planet. The company is a global leader in the fields of IoT intelligent systems and embedded platforms. To embrace the trends of IoT, big data, and artificial intelligence, Advantech promotes IoT hardware and software solutions with the Edge Intelligence WISE-PaaS core to assist business partners and clients in connecting their industrial chains. Advantech is also working with business partners to co-create business ecosystems that accelerate the goal of industrial intelligence.”
Vulnerable versions
EKI-1524-CE series / 1.21 (CVE-2023-4202)
EKI-1522-CE series / 1.21 (CVE-2023-4202)
EKI-1521-CE series / 1.21 (CVE-2023-4202)
EKI-1524-CE series / 1.24 (CVE-2023-4203)
EKI-1522-CE series / 1.24 (CVE-2023-4203)
EKI-1521-CE series / 1.24 (CVE-2023-4203)
Vulnerability overview
1) Stored Cross-Site Scripting (XSS) (CVE-2023-4202, CVE-2023-4203)
Two stored cross-site scripting vulnerabilities has been identified in the firmware of the device. The first XSS was identified in the “Device Name” field and the second XSS was found in the “Ping” tool. This can be exploited in the context of a victim’s session.
Proof of Concept
1) Stored Cross-Site Scripting (XSS)
Both cross-site scripting vulnerabilities are permanently affecting the device.
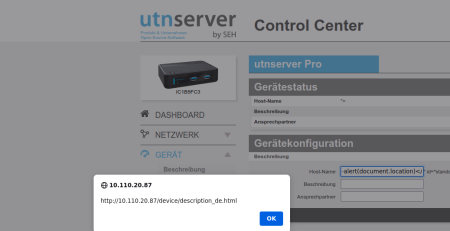
1.1) Stored XSS in Device Name CVE-2023-4202
The first vulnerability can be triggerd by setting the device name
(“System->Device Name”) to the following value:
“><script>alert(“document.cookie”)</script>
This code prints out the cached cookies to the screen.
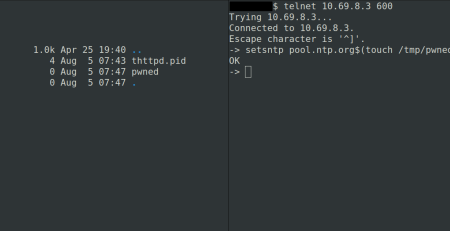
1.2) Stored XSS in Ping Function CVE-2023-4203
The second XSS vulnerability can be found in “Tools->Ping”. The following GET request prints the current cached cookies of a user’s session to the screen.
http://$IP/cgi-bin/ping.sh?random_num=2013&ip=172.16.0.141%3b%20<script>alert(1)</script>&size=56&count=1&interface=eth0&_=1682793104513
An alternative to the used payload is using “onmouseover” event tags. In this case it prints out the number “1337”: ” onmousemove=”alert(1337)
Approach
The vulnerability was manually verified on an emulated device by using the MEDUSA scalable firmware runtime (https://medusa.cyberdanube.com).
Solution
Upgrade to the newest available firmware.
Workaround
None.
Recommendation
CyberDanube recommends Advantech customers to upgrade the firmware to the latest version available.
References
Contact Timeline
- 2023-05-16: Contacting vendor via security contact.
- 2023-05-24: Contact stated that issue 1.1) is solved after firmware v1.21.
The contact is trying to reproduce issue 1.2; Gave advice to reproduce issue. - 2023-05-25: Contact stated that new firmware should resolve the issue.
- 2023-06-03: Sent new payload to the vendor.
- 2023-06-05: Vendor asked for clarification; Sent further explaination to the contact; Vendor contact said he knows a solution.
- 2023-06-22: Asked for an update; Contact stated that the beta firmware should resolve the issues.
- 2023-06-27: Asked for the release date.
- 2023-07-04: Contact stated, that they are currently doing QA tests.
- 2023-07-06: Asked if issue 1.1 is really resolved to be released; Vendor stated that it can be published.
- 2023-07-17: Assigned CVE numbers for the issues. Asked for an update.
- 2023-07-18: Vendor contact stated that the firmware will be released end of July.
- 2023-08-07: Asked contact for the new firmware version.
- 2023-08-08: Received version 1.26 as the official released firmware with fixes.
Coordinated release of security advisory.
Author
UAS St. Pölten, short for University of Applied Sciences St. Pölten, is a renowned institution of higher education located in St. Pölten, Austria. Known for its focus on practical education and innovative research, UAS St. Pölten offers a wide range of programs across various disciplines.
Recently, during a lecture of CyberDanube, conducted at UAS St. Pölten, students discovered cybersecurity vulnerabilities. This research was made possible by the support and coordination provided by CyberDanube & the MEDUSA solution.